What is PDF DRM?
Digital Rights Management (DRM) is a technology used to control the use and distribution
of digital content, such as e-books, music, and videos. DRM for PDFs works by encrypting
the content of the file and then controlling access to the decryption key. Here are some
key concepts and best practices for using DRM to secure PDFs.
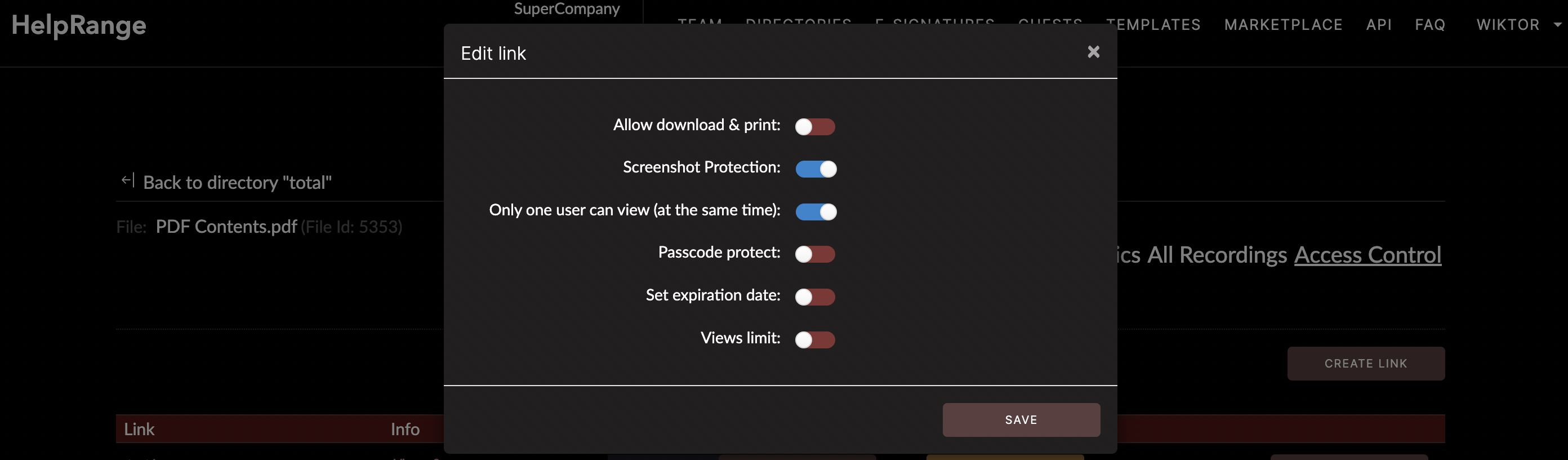
Password protection
One of the most basic and effective ways to secure a PDF is to add a password to it.
This ensures that only those who know the password can open and view the contents of the
file. When creating a password-protected PDF, you can specify whether the password is
required to open the file, or if additional permissions, such as editing or printing,
are also protected.
Encryption
DRM for PDFs typically uses encryption to protect the contents of the file. This means
that without the appropriate decryption key, the contents of the file will be
unreadable. The encryption algorithm used will depend on the specific DRM solution, but
AES is commonly used for this purpose.
Key management
To control access to the decryption key, DRM systems use key management servers. These
servers are responsible for distributing the decryption key to authorized users, and
revoking access if necessary. Key management servers also ensure that the key is only
used by authorized devices and software.
User authentication
To access the decryption key, users must first be authenticated by the DRM system. This
typically involves providing a username and password, but can also include other methods
such as biometric authentication or hardware tokens.
Usage rights
DRM systems can be configured to enforce various usage rights, such as the number of
times a document can be viewed or printed, or the duration of access. These usage rights
are typically enforced by the key management server.
Licensing
DRM systems also manage licensing of the content, ensuring that the content is only used
in accordance with the terms of the license. This can include things like how many users
can access the content and for how long.
Trusted Platform
DRM solution should be implemented on a trusted platform, such as a server or a cloud,
that is secure and managed by a reputable provider.
A Few Words Of Summary
By using DRM to secure PDFs, you can control access to the content and ensure that it is
used in accordance with the terms of the license. However, it's worth noting that DRM
can also make it more difficult for legitimate users to access the content, and that it
can be circumvented by determined attackers. We can help you in that. We built tool to
protect your PDFs. It is called HelpRange.
Check out HelpRange
HelpRange is "Next-Gen Data Room For Documents Protection & Analytics". HelpRange is a cutting-edge virtual data room platform for document access controls and in-depth analytics, ensuring superior management and usage insights for your documents.
